Hours before Russian hacking operations targeted Hillary Clinton’s campaign in the spring of 2016, WikiLeaks discussed offering a monetary reward for transcripts of her speeches at Goldman Sachs. Soon after, Russian hackers launched a spear phishing campaign that resulted in John Podesta’s email account being compromised. Emails containing excerpts from the speeches were included in the first day of the Podesta email releases. A week later, emails containing the transcripts themselves were released. WikiLeaks heralded these transcripts as their “holy grail.”
The story began on March 9, 2016, when WikiLeaks sent a tweet with a poll asking if they should add Hillary Clinton’s Goldman Sachs speeches to their ”Most Wanted” page for six figure rewards for materials. When the poll completed twenty four hours later, 93% of respondents said that WikiLeaks should offer a reward for the speeches. The Russian hackers at Fancy Bear may have been listening and been inspired by WikiLeaks’ comment. Unpublished targeting data collected by Secureworks shows the hacking campaign began earlier than the Mueller indictment reveals. A week and a half later, after dozens of attempts to penetrate the accounts of Podesta and other Clinton staffers and associates, Fancy Bear sent the phishing email that successfully tricked Podesta into compromising his account and the Goldman Sachs speeches along with it.
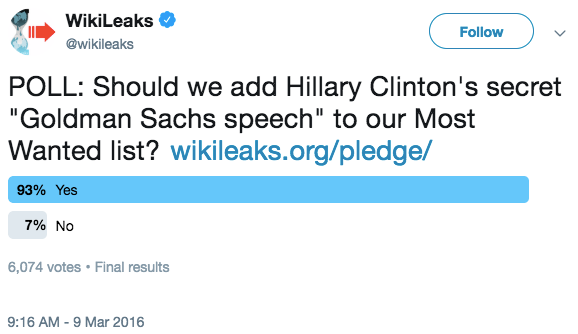
Secureworks’ unpublished breakdown of the Russian spear phishing and hacking effort, which AP described last year, shows that the campaign to penetrate the account began hours after WikiLeaks teased the possibility of offering a reward for the information. The tweet first mentioning the potential of a reward for the Goldman Sachs transcripts was sent at 8:16 P.M. Moscow time. At 11:56 AM the next day, less than sixteen hours later, Russian hackers began a campaign that would target “over 300 individuals affiliated with the Clinton Campaign, DCCC, and DNC.“ Podesta’s emails accounts were targeted in the days that followed and successfully compromised a week later, resulting in the exfiltration of nearly 60,000 emails.

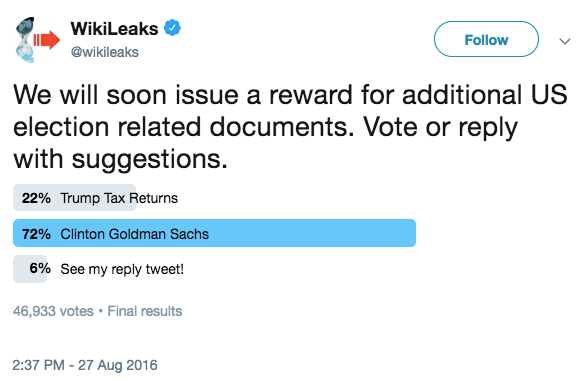
Months after they tweeted about a possible reward for the Goldman Sachs speeches, WikiLeaks tweeted that they would soon offer a reward for additional documents related to the U.S. election. Attached to the August 27 tweet was a poll asking if it should be the Goldman Sachs transcripts, Trump’s tax returns, or something else. 72% of the it’s nearly 47,000 respondents voted for the Goldman Sachs transcripts. WikiLeaks doesn’t appear to have formally offered the reward, though they defended their decision to do so in a subsequent tweet. The organization’s defense of their use of rewards addressed questions of efficacy, but not questions of the ethics. Many organizations shy away from such rewards not simply because they can induce sources to fabricate, but because they can induce sources to take illegal action to get the information. While some Democrats have offered rewards for copies of Trump’s tax returns, they specify that they must be legally obtained.
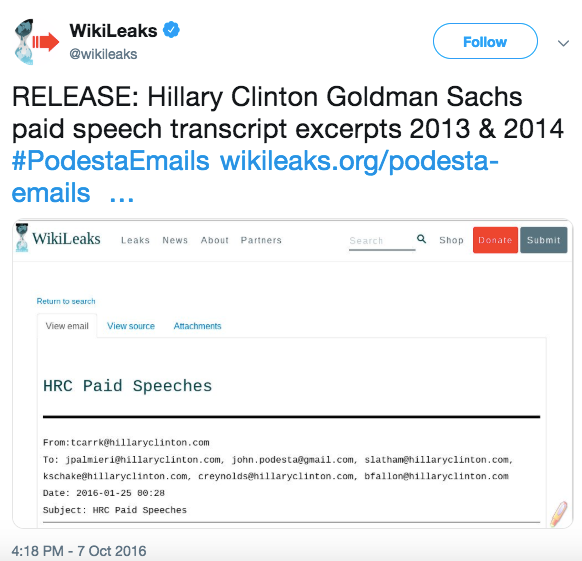
By the second time WikiLeaks brought up a reward for the Goldman Sachs transcripts, they were already in touch with the Russian hackers through the Guccifer 2.0 front. According to the Mueller indictment, the organization had made contact with them at least two months prior and received the DNC emails a few later. However, it’s not yet clear precisely when the organization received the Podesta emails or learned they contained copies of the Goldman Sachs transcripts, though the metadata indicates they may have been transferred on September 19th. Regardless of when WikiLeaks received the Podesta cache, the emails containing the Goldman Sachs speeches were among the first emails that the organization chose to release. To emphasize the release of the excerpts, WikiLeaks tweeted a link and picture highlighting the email that contained excerpts from Clinton’s 2013 and 2014 speeches at Goldman Sachs.
A week later, WikiLeaks released transcripts of three of Clinton’s Goldman Sachs speeches. In one of their tweets, they referred to it as a “holy grail” of journalism.

The handful of waking hours in Moscow separating WikiLeaks’ proposal of offering a reward for the Goldman Sachs speeches and the beginning of a new wave of spear phishing attempts is not the only time Russian hackers may’ve taken their cue from the calls for the release of Hillary Clinton material. On July 27, 2016, Donald Trump infamously and publicly encouraged Russians to provide copies of Hillary Clinton’s emails. Trump’s call to action was made when it was late afternoon in Russia, and was followed by some “after-hours” spear phishing.
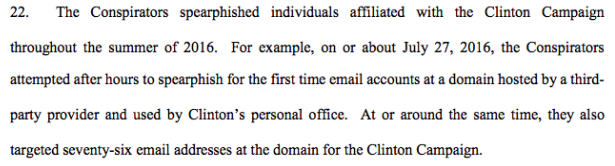
The timing of the two events suggestively points to a possible connection between WikiLeaks’ willingness to reward stolen Clinton information with the decision by Russian intelligence to steal Clinton information. However, prosecutors would likely face difficulties making a case for solicitation based solely on the discussion of a potential reward. The discussion does, however, provide a basis for further investigation by authorities.
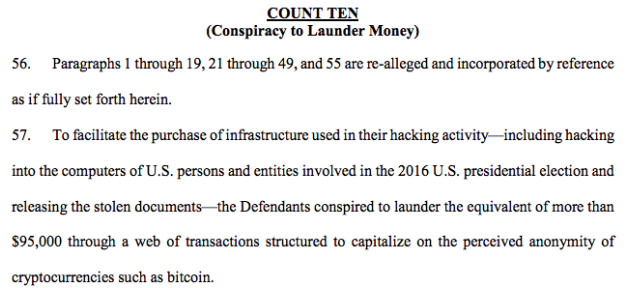
The FBI and Robert Mueller’s office have, for instance, identified bitcoin accounts used by the Russian hackers for the campaign targeting the 2016 U.S. Presidential election as well as their preexisting efforts targeting diplomats, diplomatic institutions and persons of interest to Russian intelligence. The web of transactions associated with those accounts have undoubtedly been scoured for any connections to WikiLeaks, as have the organizations’ other communications.
Regardless of whether the mention of a reward factors into discussions within the Department of Justice about whether and how to charge Assange and other WikiLeaks personnel, it is the sort of behavior that’s come to the attention of the Central Intelligence Agency. In a speech on July 7, 2017, CIA Director Pompeo said that “WikiLeaks [is] a non-state hostile intelligence service that recruits spies, rewards people who steal legitimate secrets, and uses that information to subvert Western democracies.” The Director’s comments may have been general observations, though it’s unlikely that the Agency would be aware of this behavior but not consider the timing of the two events.
Even if investigators found no information to reinforce the timing connection (such as an actual payment), it raises ethical questions in the debate surrounding WikiLeaks. In the past, the organization’s response to the question has focused on veracity of materials, but ignored the implications of creating incentives to find and submit private or secret materials. In this instance, the result is a series of events the timing of which suggest that WikiLeaks’ tweet may have been the inspiration for beginning the next phase of Russia’s cyberwar operations.
While contentious, the ethical questions are far from one-sided. A New York Times op-ed addressed the situation in 2015 with cautious praise, calling it “a flawed solution to a very real problem.” The op-ed also warned that “it seems probable that WikiLeaks will entice someone into breaking the law.” “The idea of offering a cash incentive for the leaking of confidential documents is anathema. But WikiLeaks, like other media disrupters [sic], leaves us no choice but to reconsider this prohibition.” Despite its cautiously high praise, the op-ed provides a nuanced glimpse of a debate that’s sure to be renewed by the timing of WikiLeaks’ tweet and the onset of Russian cyber attacks targeting Hillary Clinton.
Other questions also remain – was it a coincidence that the Podesta emails WikiLeaks received contained the Goldman Sachs speeches they were interested in? Numerous other emails and documents were released through the DCLeaks front and the Guccifer 2.0 entity, raising the question of why these specific emails were reserved for WikiLeaks. Did WikiLeaks argue, as Mueller and BuzzFeed have documented in other instances, that it would have more impact if WikiLeaks had exclusivity? These questions are somewhat typical of the ones resulting from the investigation into interference with the 2016 election – they boil down to separating coincidence from complicity. For WikiLeaks, that question is not just a legal one, but a moral one.
Update: A clarification was added regarding the date in the Podesta emails metadata.